Two Factor Authentication
Two-factor authentication (2FA) refers to the two step verification process that is available in FileCloud and designed to provide an extra layer of security. With this function, in order to access FileCloud, the user is required to know not only the password and username but also an extra security code that is made available to them. The FileCloud administrator can enable two-factor authentication and require it for access to the user portal. This can be done regardless of the authentication type (default, AD, or LDAP).
FileCloud supports the following modes to deliver 2FA codes:
- Deliver code using user's registered email
- Google Authenticator TOTP Code
- DUO Security
- SMS OTP Security Code
Two-factor authentication into user portal using user's registered email address
The general flow is shown below
Two-factor authentication in user portal using TOTP (Google Authenticator or similar TOTP code generators)
These instructions are written using Google Authenticator as an example TOTP code generator, however, any TOTP apps such as Microsoft Authenticator or DUO mobile app, etc. can be used.
To set up 2FA with Google Authenticator, simply choose TOTP (Authenticator App) when configuring 2FA for the user portal. See Enable Two Factor Authentication for User Portal (Global setting), below, for help.
When the user logs in to the user portal for the first time, the user will be provided with an option to set up Google Authenticator. This involves entering a code or scanning a QR Code into the the Google Authenticator client. See Log in Using Two-Factor Authentication for more information.
Note that once Google Authenticator is set up using the user portal, other client devices can be used to connect to the FileCloud account.
Once 2FA with Google Authenticator is set up for the first time the user will no longer be able to set it up again. Only the Administrator can clear the Google Authenticator setup.
Instead of Google Authenticator app, Microsoft or Duo Security apps can also be used to manage the TOTP code
The general flow is shown below
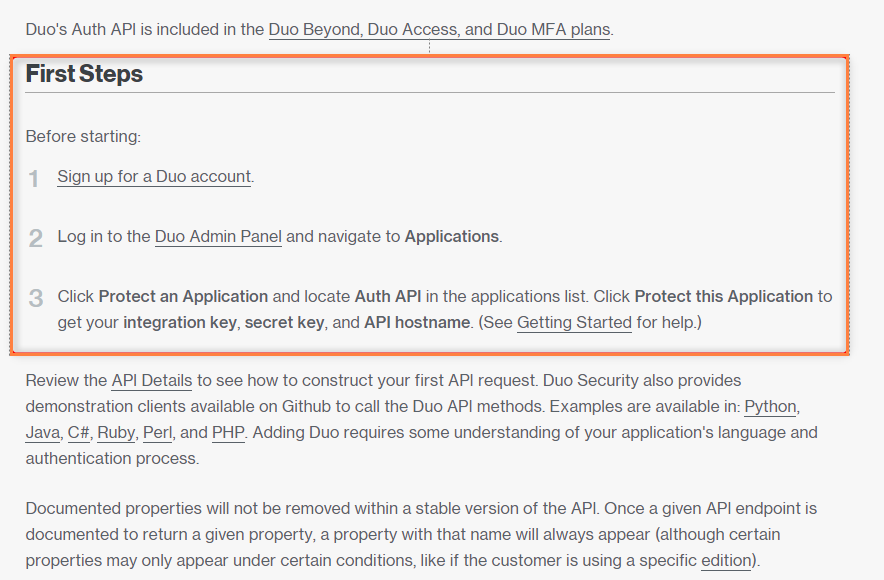
Two-factor authentication using DUO security
The following steps are required to setup 2FA using DUO
- ADD DUO Auth API
- Follow instructions at https://duo.com/docs/authapi to get integration key, secret key, and API hostname.
- Follow instructions at https://duo.com/docs/authapi to get integration key, secret key, and API hostname.
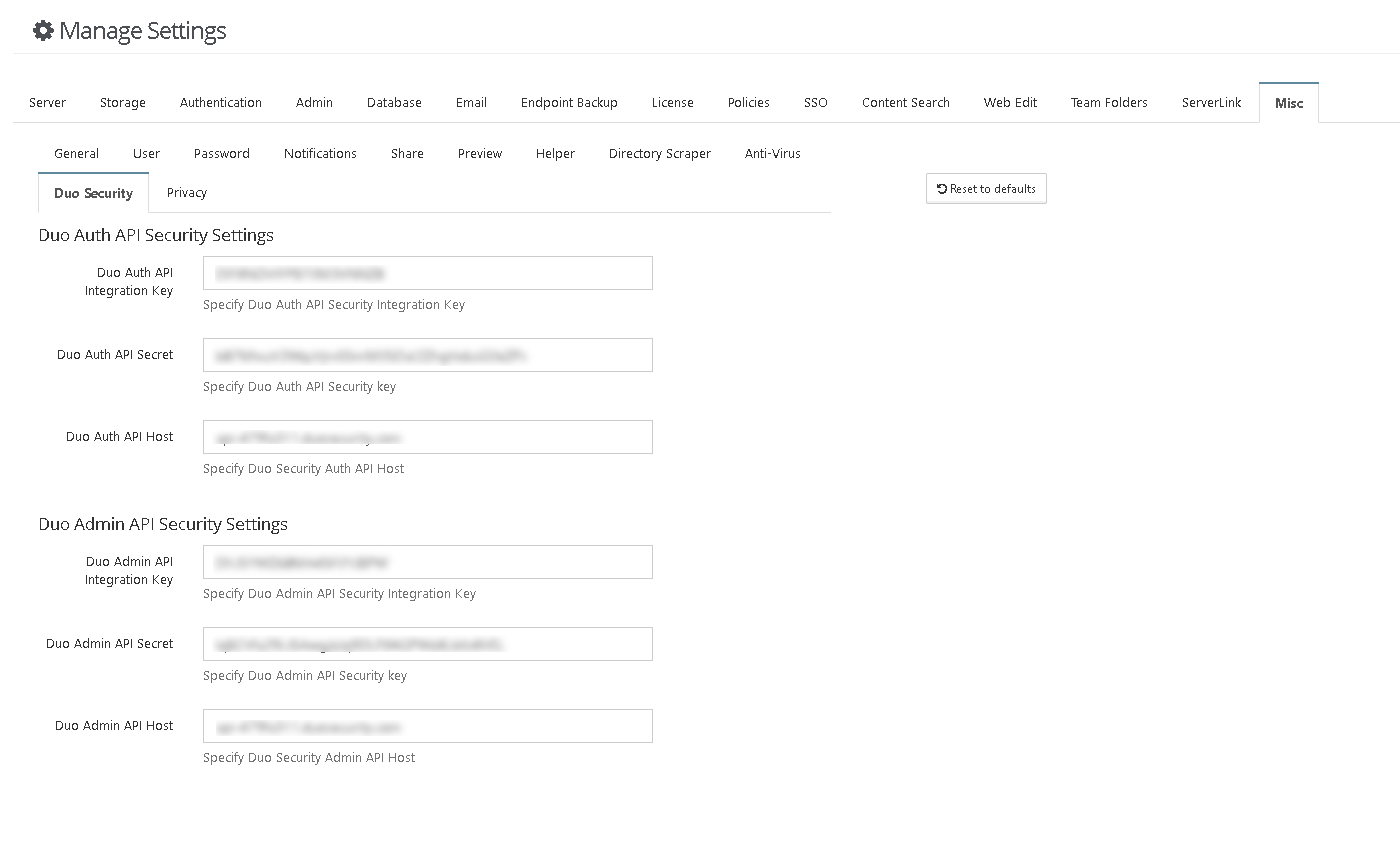
- In the FileCloud Admin portal, enter the information in Settings > Misc > Duo Security tab under Duo Auth API Security Settings, and save.
- In the FileCloud Admin portal, enter the information in Settings > Misc > Duo Security tab under Duo Auth API Security Settings, and save.
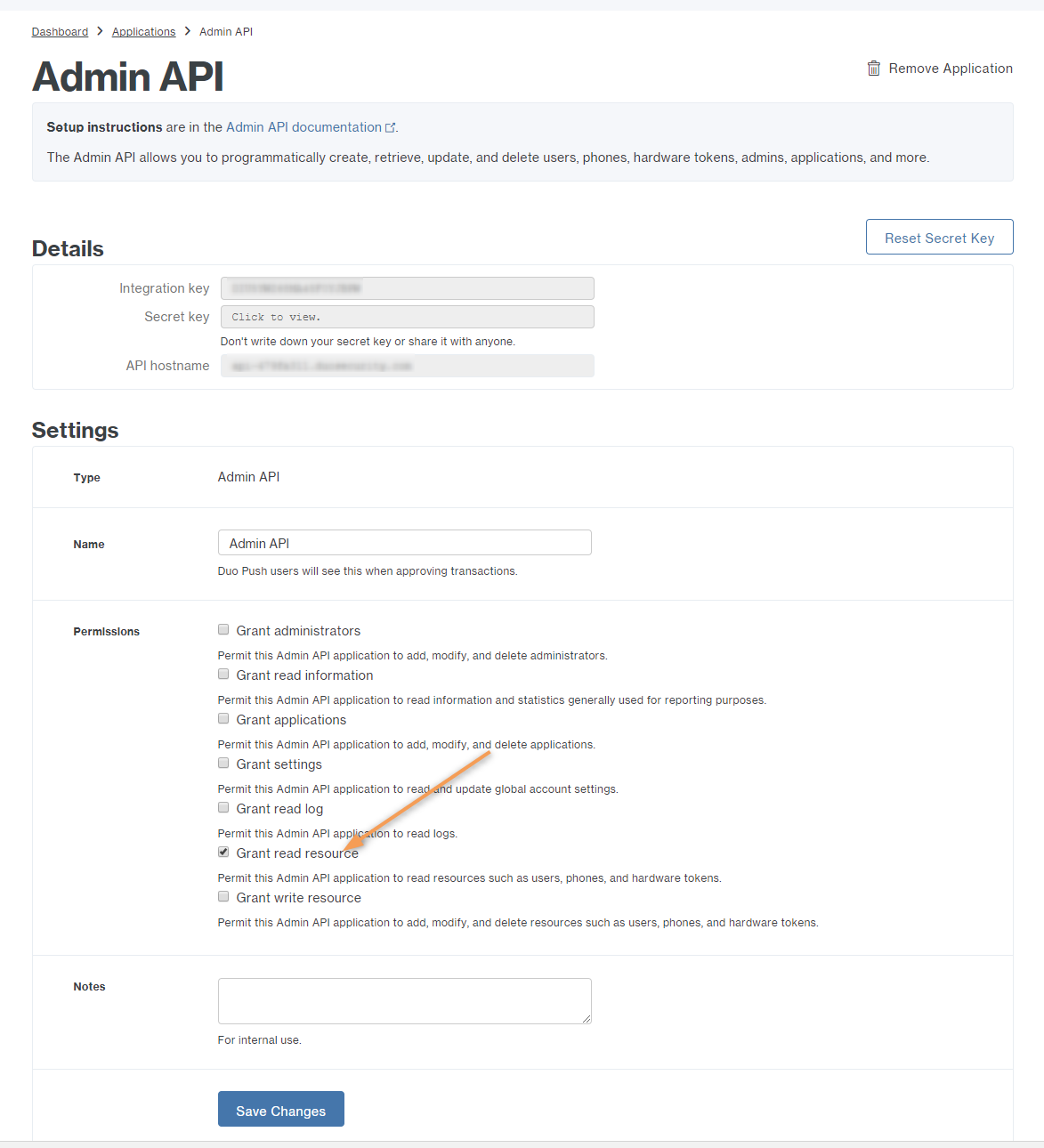
- Add DUO Admin API
- Follow instructions at https://duo.com/docs/adminapi to get values for integration key, secret key, and API hostname
- Ensure it has "Grant read resource" permission.
- In the Admin portal, enter the information in Settings > Misc > Duo Security under Duo Admin API Security Settings, and save.
- Open the Policies tab and select the policy (Select the Global policy if 2FA needs to be the default )
- Open the 2FA tab of the Policy.
- Select "YES" for Enable Two Factor Authentication
Select "DUO Security" for Two Factor Authentication Mechanism and save the policy.
Now, users are required to use 2FA to log in through the user portal.
Note: When users who are enrolled in the Duo Admin Panel log in, they must use the text code from the default entry in their Duo App. When users who are not enrolled in the Duo Admin Panel attempt to log in, they are prompted to use a QR code scanner to enroll themselves, and then must use the text code from the entry they added in their Duo App. See Log in Using Two-Factor Authentication for more information.
Two-factor authentication using SMS OTP (one-time password) Security Codes
As of v19.2, FileCloud can be set up to use SMS security codes to perform 2FA. Currently, we have implemented Twilio as the default SMS Gateway Provider, although enterprise customers may add custom SMS providers and handlers to the system. In order to successfully use SMS security, admins must set up a Twilio account to receive the required security ID, authentication token and the phone number from which the codes will be sent.
- Create a Twilio account
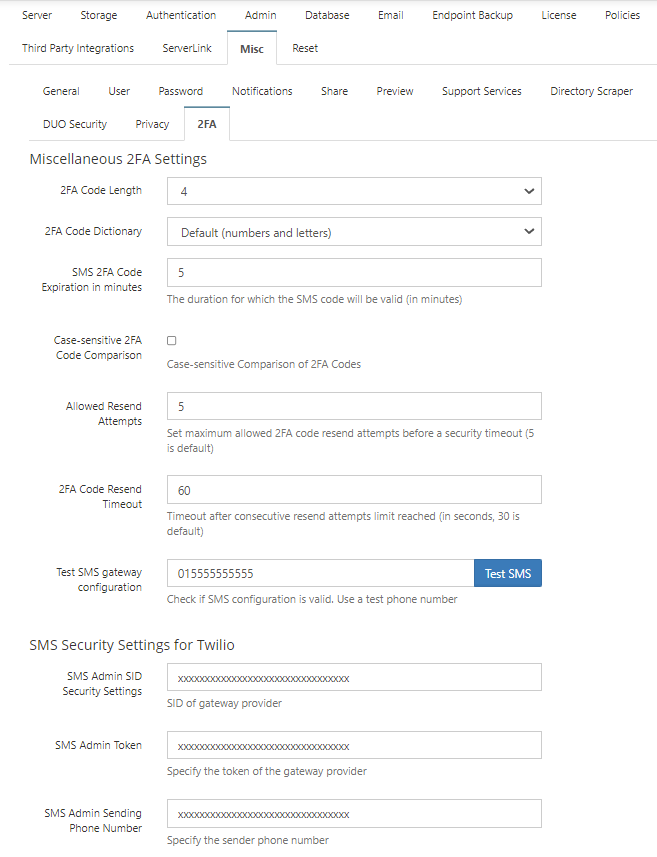
Follow instructions at https://www.twilio.com/docs/sms to obtain the required SID, Auth Token and create a phone number. Enter the information in Settings > Misc > 2FA.
The settings 2FA Code Length and 2FA Code Directory are available beginning in FileCloud version 20.2.
2FA Code Length - The number of letters and digits in the 2FA code. Default is 4.2FA Code Dictionary- Type of characters permitted in 2FA code. Options are:
- Numbers and letters (default)
- Numbers
- Letters
- Uppercase letters
SMS 2FA Code Expiration in Minutes - How long, in minutes, the security code remains valid. Default is 10.
Case-sensitive 2FA Code Comparison - When checked, the code entered is case-sensitive.
Allowed Resend Attempts - Number of times the user may resend the code before logging in is timed out for the time set in 2FA Code Resend Timeout.. Default is 5.
2FA Code Resend Timeout - Number of seconds between Allowed Resend Attempts that the user must wait before attempting to resend again. Default is 30.
For example, if Allowed Resend Attempts is 5, and 2FA Code Resend Timeout is 30, a user can attempt to resend a code 5 times and then is forced to wait 30 seconds before being able to attempt to resend the code another 5 times. If those attempts fail, the user is forced to wait another 30 seconds, and so on.Test SMS Gateway Configuration - Enter a secure known phone number, and save the settings. Click Test SMS to check if your SMS configuration is valid.
SMS Admin SID Security Settings - SID of gateway provider.
SMS Admin Token - Token of gateway provider.
SMS Admin Sending Phone Number - Phone number from which SMS code is sent to user.
Once the setup is complete, set up the policy for users and choose the appropriate SMS gateway provider, similarly to other 2FA methods.
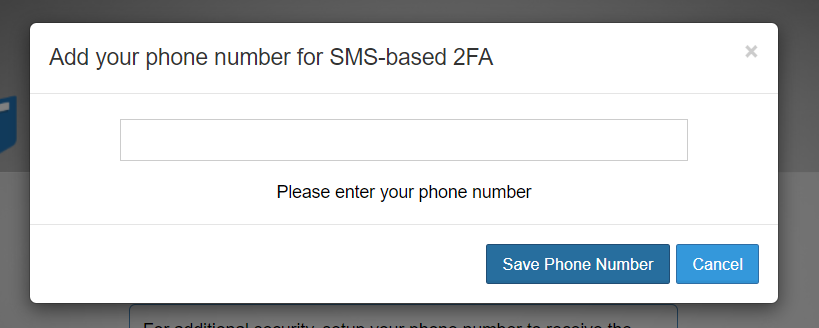
Users are required to set up a phone number once the SMS 2FA Policy is enabled. Once the phone number is set up, client devices can be used to connect to the FileCloud account. Set up the phone number via the web UI or through your admin.
If users are required to use SMS with 2FA, they will see the following dialog box during login after the policy is enabled:
Enable Two-Factor Authentication using SMS OTP Security Codes for specific user agents
Starting with Version 19.3, FileCloud supports configuring two-factor authentication using SMS OTP for specific user agents. For example, you could apply this configuration to mobile clients only, or to FileCloud Drive, FileCloud Sync, and Microsoft Outlook only.
- Complete the instructions above in Two Factor Authentication using SMS OTP Security Codes
Open cloudconfig.php at
Windows: XAMPP DIRECTORY/htdocs/config/cloudconfig.php
Linux: /var/www/config/cloudconfig.php
Add the following:
define("TONIDOCLOUD_TWOFA_REQUIRED_USERAGENT_LIST", "useragent1,useragent2, ... ");Replace the useragent values with any number of user agents from the following list:
Web browser
Android
iOS
MS Outlook
MS Office
MS Office Online
Cloud Sync
Starting with Version 19.3 of FileCloud use: FileCloud Drive
Prior to Version 19.3 of FileCloud use:
FileCloudDrive or FileCloudDrive2
FileCloud MacDrive or FileCloud MacDrive2Any white labelled FileCloud Sync/Drive product name
For example:define("TONIDOCLOUD_TWOFA_REQUIRED_USERAGENT_LIST", "Android,iOS");
Enable Two Factor Authentication for User Portal (Global setting)
Administrator can enable Two Factor Authentication using the following steps
- Log into the Administrator Portal
- Navigate to "Settings"
- Select Polices Tab
- Under 2FA heading, Change the Enable Two Factor Authentication drop down box to Enabled
In Two Factor Authentication Mechanism choose Email, TOTP (Authenticator App), DUO Security or SMS Security.
6. If you choose SMS Security and users are permitted to create accounts, add the following setting that enables users to add a phone number when creating a share with an external user:
- Open the configuration file:
Windows: XAMPP DIRECTORY/htdocs/config/cloudconfig.php
Linux: /var/www/config/cloudconfig.php Add the line:
define ("TONIDOCLOUD_ENABLE_2FA_SMS_SHARE_INVITES", TRUE);
- Open the configuration file:
Reset TOTP or DUO settings for a user
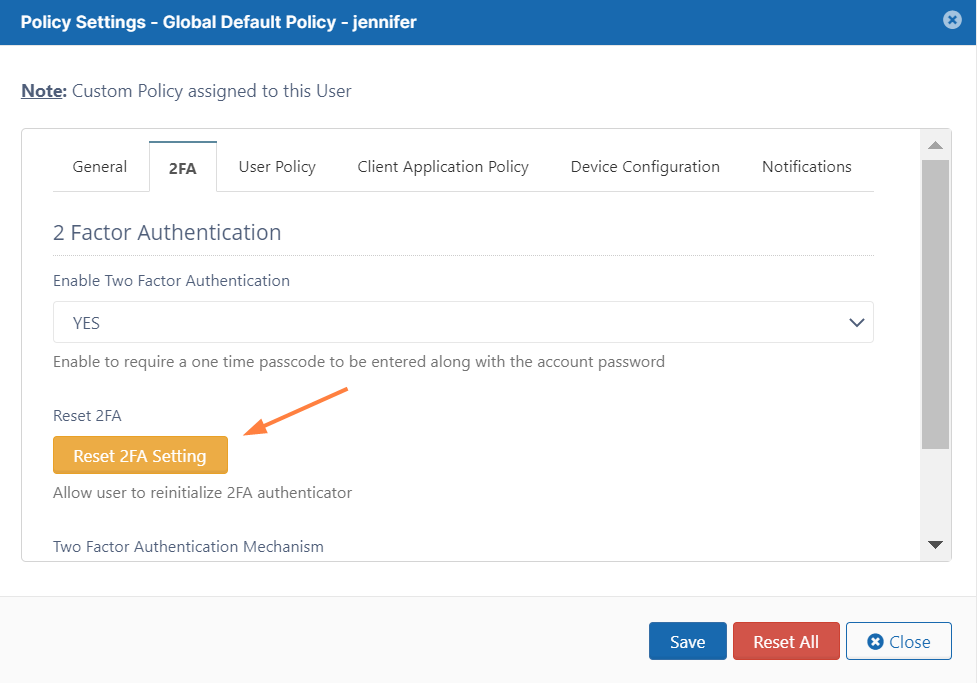
When a user loses a TOTP (Google Auth) app enabled device or if they need to reset the code for any reason, the Admin can reset the Google Authenticator setup for that user using the following steps
- Login into the Admin portal
- Navigate to Users and click the Manage Policy icon in the row for the user.
- Click the 2FA tab.
- Click the Reset 2FA Setting to enable the user to reset their authenticator code.
After the secret is reset, the user is not required to redo the DUO 2FA setup on initial login as FileCloud will import access tokens from DUO automatically.
New devices can be registered from the DUO Admin Panel using the DUO Enrollment Email feature.
Two factor authentication validity for Email based 2FA
2FA Code validity: 10 minutes.
This can be changed by adding a key with a different timeout as shown (This key can be added <WEBROOT>/config/cloudconfig.php).
define ("TONIDOCLOUD_2FA_EMAIL_EXPIRATION_MINUTES", "5");
For Web Apps, The 2FA validity period is tied to the Session Timeout
For Client apps (iOS , Android App, Drive and Sync) the 2FA code will be required only on very first access and subsequent access will not require the code. If the record of that device is removed using "Remove Client Device Record" action, then subsequent access for that mobile device will require the 2FA code.
Two-Factor Authentication for Admin Portal
From v12 onwards, support for two factor authentication is available for Admin portal. Both site admin and super admin (for multi tenancy control panel) can be set to require additional code in order to access.
Two factor authentication for Admin supports only Email based 2FA. The code will be delivered to the email associated with the account.
Since 19.2, the way admins set up 2FA has changed - the admin can now select code sendout methods using a drop down (Email or SMS). In order to upgrade without hassle, it is advised to disable admin 2FA before upgrading, and set it up again.
The flow is same as user 2FA flow as shown below
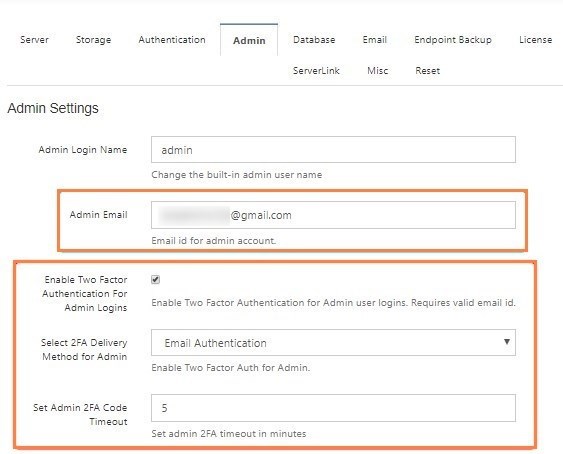
Enable Two Factor Authentication for Site Admin
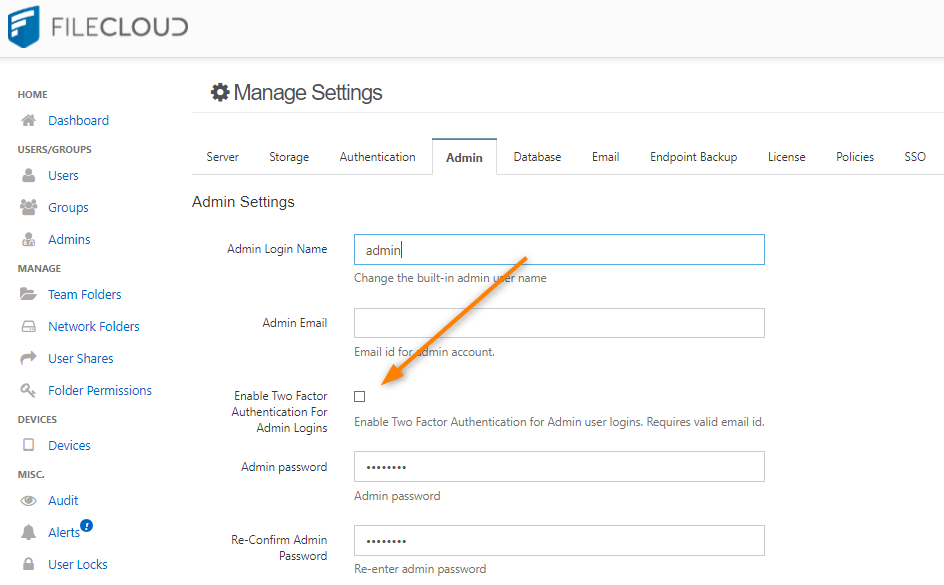
A site admin is the admin account to log into the Administrator portal of a specific site. To enable 2FA for the first time, please follow the steps
- Log into Admin portal
- Navigate to "Settings"
- Select "Admin" Tab
- Check Enable Two Factor Authentication for Admin Logins.
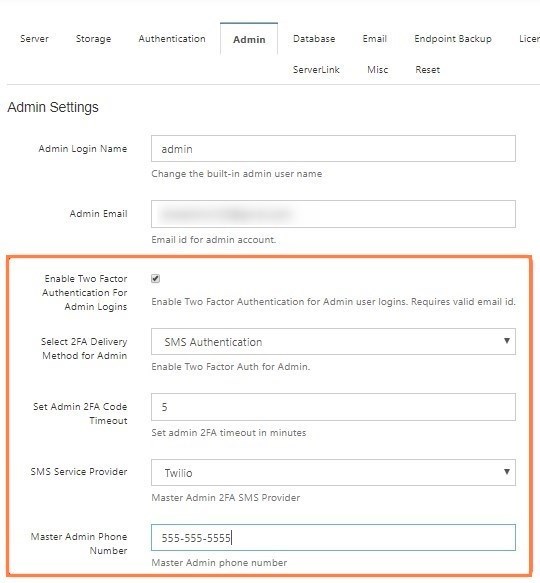
2FA fields appear. - To use SMS authentication, In Select 2FA Delivery Method for Admin, choose SMS Authentication.
Additional fields appear.- In Set Admin 2FA Code Timeout, set the time in minutes that you want the temporary log-in code to remain valid.
- In SMS Service Provider, choose Twilio or Custom.
- In Master Admin Phone Number, enter the admin's SMS phone number.
An invalid master admin phone number will cause lockout - the portal will not be accessible when SMS Authentication is chosen.
- To use email authentication, in Select 2FA Delivery Method for Admin, choose Email Authentication..
- Enter a valid email in the Enable Two Factor Authentication for Admin Logins field, above the Enable
- In Set Admin 2FA Code Timeout, set the time in minutes that you want the temporary log-in code to remain valid.
Enable Two-Factor Authentication for Super Admin for Multi-tenancy control panel access
From FileCloud v12 onwards, superadmin logins can be required to use 2FA to access the Multi-tenancy control panel.
Open "multi.php" (In ubuntu it is at /var/www/config/ and in Windows it is typically at c:\xampp\htdocs\config)
Add the lines:
define ("TONIDOCLOUD_SUPER_ADMIN_EMAIL_ID", "email@company.com");
define ("TONIDOCLOUD_ENABLE_SUPER_ADMIN_2FA","1");
In case the lines are commented "//", please remove the double slash symbol at the beginning of the line and save the changes.
Note that you need to provide valid email . If the email is invalid, then the Multi-tenancy control panel cannot be accessed.